Top Access Control Security Best Practices for Protecting Your Assets
In today’s increasingly interconnected world, the importance of Access Control Security has grown significantly, as organizations seek to protect their physical and digital assets against unauthorized access. According to a recent report by the International Security Management Association (ISMA), nearly 37% of security breaches in organizations can be attributed to inadequate access control measures. This underscores the critical need for robust systems that not only regulate who can access sensitive areas but also track and manage these interactions effectively.
Industry expert John Doe, a renowned security analyst, emphasizes the impact of comprehensive access control systems by stating, “A well-implemented access control strategy is the backbone of organizational security, mitigating risks and enhancing overall safety.” As businesses face evolving threats, the integration of advanced technologies—such as biometric authentication and real-time monitoring—is becoming essential. These technologies, combined with best practices in Access Control Security, can significantly strengthen an organization's defense against potential vulnerabilities.
As we explore the top best practices for implementing effective access control systems, it is essential to recognize that a proactive approach can not only safeguard assets but also build a culture of security awareness throughout the organization. By adopting these strategies, companies can minimize risk and protect their valuable resources, ensuring a secure environment that fosters innovation and growth.

Understanding Access Control Security: An Overview
Access control security is a critical component of asset protection, ensuring that only authorized individuals can access sensitive areas and information. The fundamental principle behind access control is to maintain the integrity, confidentiality, and availability of assets. This can be achieved through various methods, including physical barriers, electronic systems, and administrative policies. Each layer of security adds complexity and difficulty for potential intruders, making it imperative to establish a robust access control strategy.
One effective approach to access control is the implementation of role-based access control (RBAC). By assigning permissions based on individual roles within an organization, companies can ensure that employees have access only to the information necessary for their job functions, thus minimizing the risk of unauthorized access. Additionally, integrating multi-factor authentication can enhance security by requiring users to provide multiple forms of verification before gaining entry. Regular audits and updates to access permissions further strengthen security, adapting to changes in personnel or operational needs while reducing the chances of data breaches.
Identifying Assets that Require Protection
Identifying assets that require protection is a crucial first step in establishing an effective access control system. According to a report from the Ponemon Institute, 60% of organizations experienced a data breach due to inadequate asset management and protection. Identifying which assets need safeguarding begins with evaluating the critical nature of data and physical resources within an organization. High-value assets typically include sensitive customer information, intellectual property, proprietary software, and critical infrastructure components. Prioritizing these assets allows organizations to allocate appropriate security measures based on the potential impact of a breach.
Furthermore, organizations must consider the dynamic nature of their assets. The Verizon Data Breach Investigations Report highlights that 22% of breaches involved assets categorized as "unsecured," indicating a significant oversight in access control mechanisms. To minimize risks, companies should implement regular audits and asset inventories to ensure that all critical assets, both digital and physical, are recognized and secured. By maintaining an updated understanding of their asset inventory, organizations can adjust their security strategies in response to evolving threats, thereby enhancing resilience against potential breaches.
Key Principles of Effective Access Control
Effective access control is essential for safeguarding your organization's assets. The key principles of access control encompass identification, authentication, authorization, and auditing. These principles form the backbone of a robust security framework that not only protects physical assets but also valuable data and intellectual property.
Ensuring proper identification and authentication is critical. Implement multi-factor authentication (MFA) wherever possible to add an extra layer of security beyond just passwords. By requiring users to provide multiple forms of verification, you significantly reduce the chances of unauthorized access. Additionally, regularly updating access permissions and credentials can help to mitigate the risks associated with employee turnover or role changes.
Another vital principle is the principle of least privilege. Users should only be granted access to the information and resources necessary for their specific roles. This minimizes potential vulnerabilities within your system. Regular audits and access reviews can help to enforce this practice, ensuring that access levels remain appropriate as business needs evolve. Implement automation tools for reporting and monitoring access, as they can help you quickly identify and remedy unauthorized access attempts, further strengthening your access control strategy.
Implementing Multi-Factor Authentication Strategies
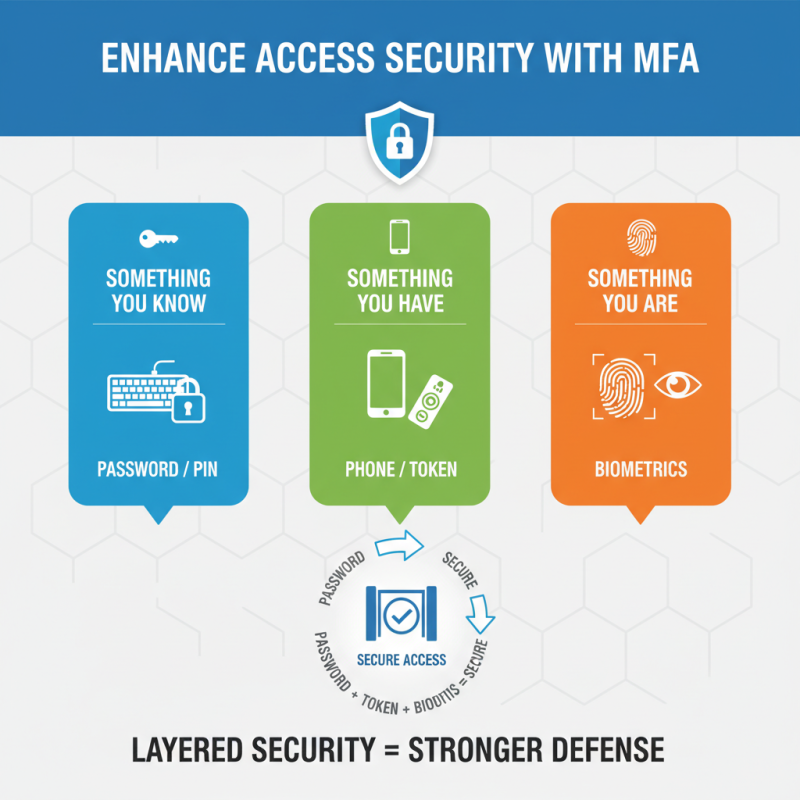
Implementing multi-factor authentication (MFA) is a crucial step in enhancing access control security practices. By requiring multiple forms of verification before granting access to sensitive assets, organizations can significantly reduce the risk of unauthorized entries. MFA combines something the user knows, like a password, with something they have, such as a mobile device, or something they are, like biometric data. This layered approach makes it exponentially harder for attackers to gain entry, as they need more than just stolen credentials.
Moreover, deploying MFA can foster a culture of security awareness among employees. By integrating authenticators that rely on various forms of identification, organizations not only protect their digital assets but also educate their staff on the importance of safeguarding sensitive information. Training employees on the operation and significance of MFA tools can lead to proactive behavior in identifying potential security threats. Implementing these practices not only fortifies an organization’s security posture but also builds trust with clients and stakeholders, showcasing a commitment to protecting their data with the highest standards of security.
Regularly Reviewing and Updating Access Policies
Regularly reviewing and updating access policies is crucial for maintaining a robust security posture in any organization. According to a report by the Ponemon Institute, organizations that regularly evaluate their access control systems can reduce the likelihood of a data breach by up to 30%. This statistic emphasizes the importance of proactive measures in protecting sensitive data and assets, as security vulnerabilities can easily evolve due to changes in the organizational structure, personnel, or technology landscape.
Additionally, the National Institute of Standards and Technology (NIST) recommends that access policies be revisited at least annually. This regular review process allows organizations to identify outdated permissions and unnecessary access rights that could lead to unauthorized data access. For instance, a study by Verizon revealed that over 80% of data breaches involved compromised credentials, highlighting the necessity of stringent access controls. By continuously updating access policies, organizations can ensure that only the right individuals have the appropriate levels of access to critical systems and information, thereby fortifying their overall security framework.
Top Access Control Security Best Practices for Protecting Your Assets
| Best Practice | Description | Frequency of Review | Responsible Party |
|---|---|---|---|
| Access Policy Review | Regular assessment and updates of access control policies to ensure they meet current security requirements. | Quarterly | Security Team |
| User Access Audits | Examine user access levels to ensure they align with job responsibilities and revoke unnecessary privileges. | Monthly | IT Department |
| Incident Response Plan Testing | Simulate security incidents to test the effectiveness of the access control measures and response protocols. | Bi-annual | Security Team |
| Training and Awareness Programs | Educate employees on access control policies and best practices to foster a culture of security. | Annual | HR Department |
| Multi-Factor Authentication Implementation | Ensure access to sensitive systems requires multi-factor authentication to enhance security. | Continuous | IT Department |
Related Posts
-

Unlocking Safety and Convenience with the Best Access Control Security Solutions
-

Unlocking the Advantages of Access Control Security for Global Procurement
-

Unlocking Business Opportunities with Access Control Software at the 138th Canton Fair 2025 in China
-

Understanding the Benefits of Biometric Attendance Machines for Modern Workplaces
-

5 Digital Strategies to Optimize Your Best Access Control System Purchase
-

Why Fingerprint Time Attendance is Essential for Modern Workforce Management